tnc-ifmap Plugin
Purpose
The tnc-ifmap plugin for libcharon enables a strongSwan VPN gateway to
act as a Metadata Access Point (MAP) Client sending its
Network Security Metadata via the SOAP 1.2 based TNC
IF-MAP 2.2 interface to a MAP Server.
The plugin is disabled by default and can be enabled with the
./configure option
--enable-tnc-ifmap
Configuration
The tnc-ifmap plugin is configured using the options defined in the
charon.plugins.tnc-ifmap
section of strongswan.conf.
| Key | Default | Description [Default] |
|---|---|---|
client_cert |
Path to X.509 certificate file of IF-MAP client |
|
client_key |
Path to private key file of IF-MAP client |
|
device_name |
Unique name of strongSwan server as a PEP and/or PDP device |
|
renew_session_interval |
|
Interval in seconds between periodic IF-MAP RenewSession requests |
server_cert |
Path to X.509 certificate file of IF-MAP server |
|
server_uri |
[→] |
URI of the form |
username_password |
Credentials of IF-MAP client of the form |
TLS Options
The tnc-ifmap plugin uses the strongSwan libtls library that can be
configured and fine-tuned with the following TLS options.
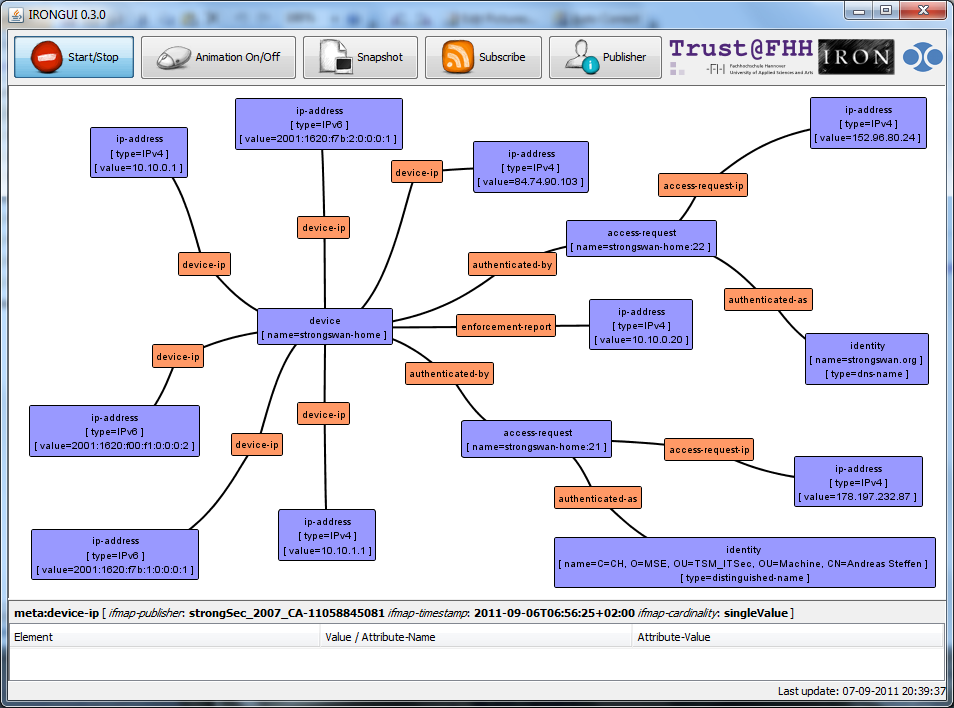
Metadata
Currently a strongSwan VPN gateway acting as a Police Enforcement Point (PEP) and additionally as a Policy Decision Point (PDP) provides the following metadata to a MAP server:
| Metadata | Description |
|---|---|
device-ip |
All IPv4 and IPv6 network interfaces the IPsec PEP listens on |
access-request-ip |
The IPv4 or IPv6 address of the remote access peer |
authenticated-as |
Identity of the remote access peer |
authenticated-by |
Device name of the PDP authenticating the remote access peer |
capability |
Group memberships of the remote access peer (assigned by RADIUS or TNCS) |
enforcement-report |
Report failed authentication of a remote access peer |
Visualization
The strongSwan MAP client sends its metadata via the TNC
IF-MAP 2.2 interface to an irond MAP server. The
irongui MAP client is attached to the irond
MAP server and visualizes the collected metadata.