Measured Boot
Using Remote Attestation, the pre-boot phase based on the BIOS/UEFI and the
ensuing bootload process are measured, certified by the Trusted Platform Module
(TPM) residing on the endpoint.
strongTNC Remote Attestation Database
TPM BIOS Measurement Policy
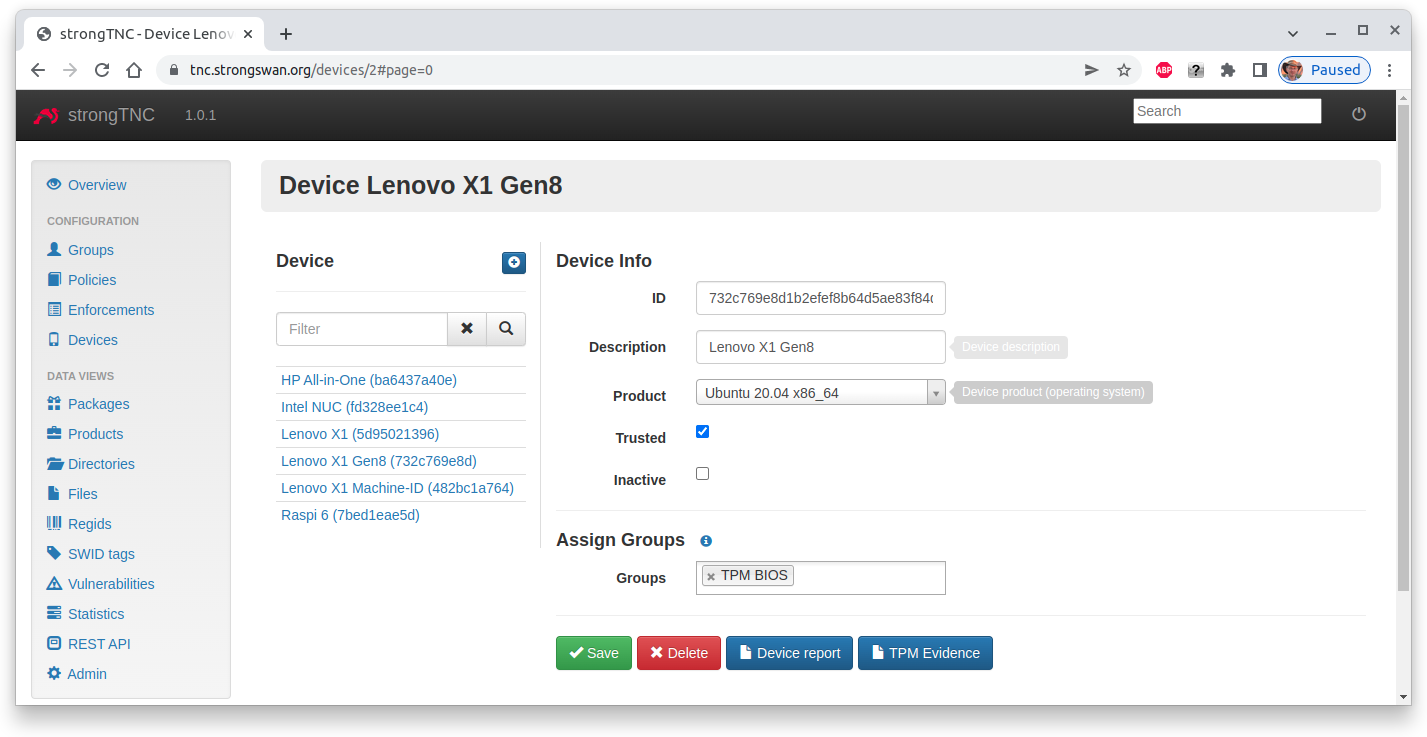
In order to enable BIOS measurements, add the TPM BIOS group in the Device
Info menu for a given device. Additionally set the Trusted flag in order to
put trust into the Attestation Key sent by the endpoint via the PA-TNC protocol.
The Device ID is the keyid of the AK, so that the correctness of the public
key can be verified.
Device Report
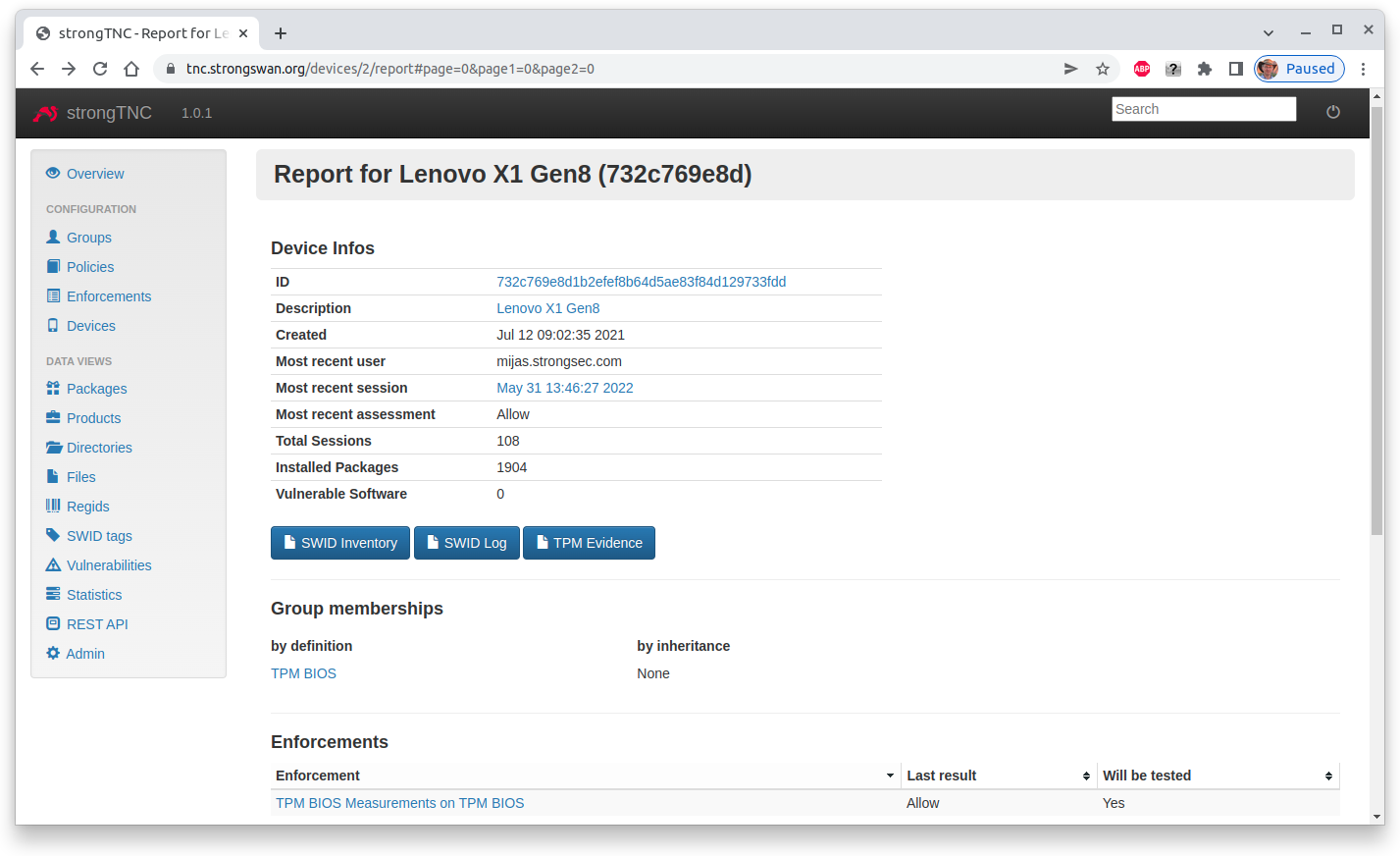
After the first run, the device report shows that a signed TPM-based BIOS measurement has been successfully retrieved from the remote device.
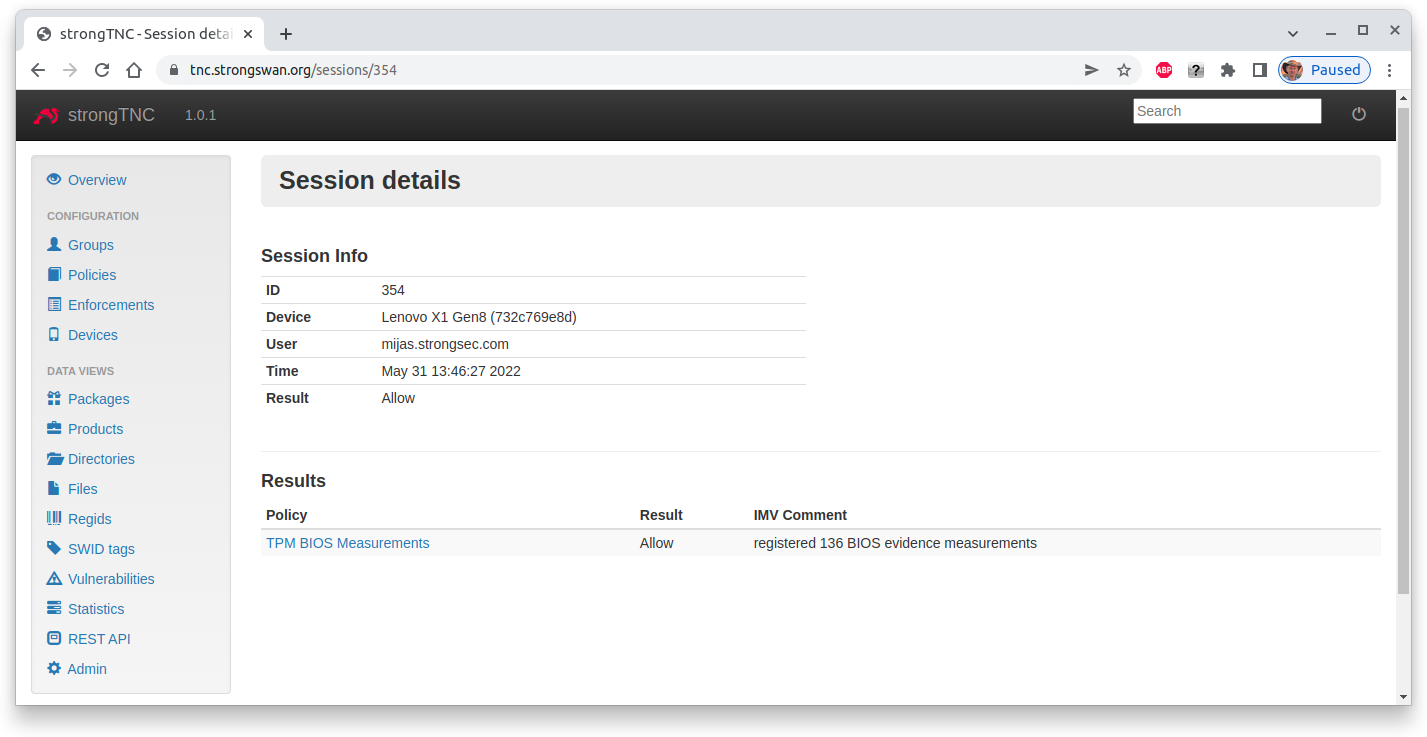
The session details show that during the first run 136 BIOS measurements have been registered in the strongTNC database.
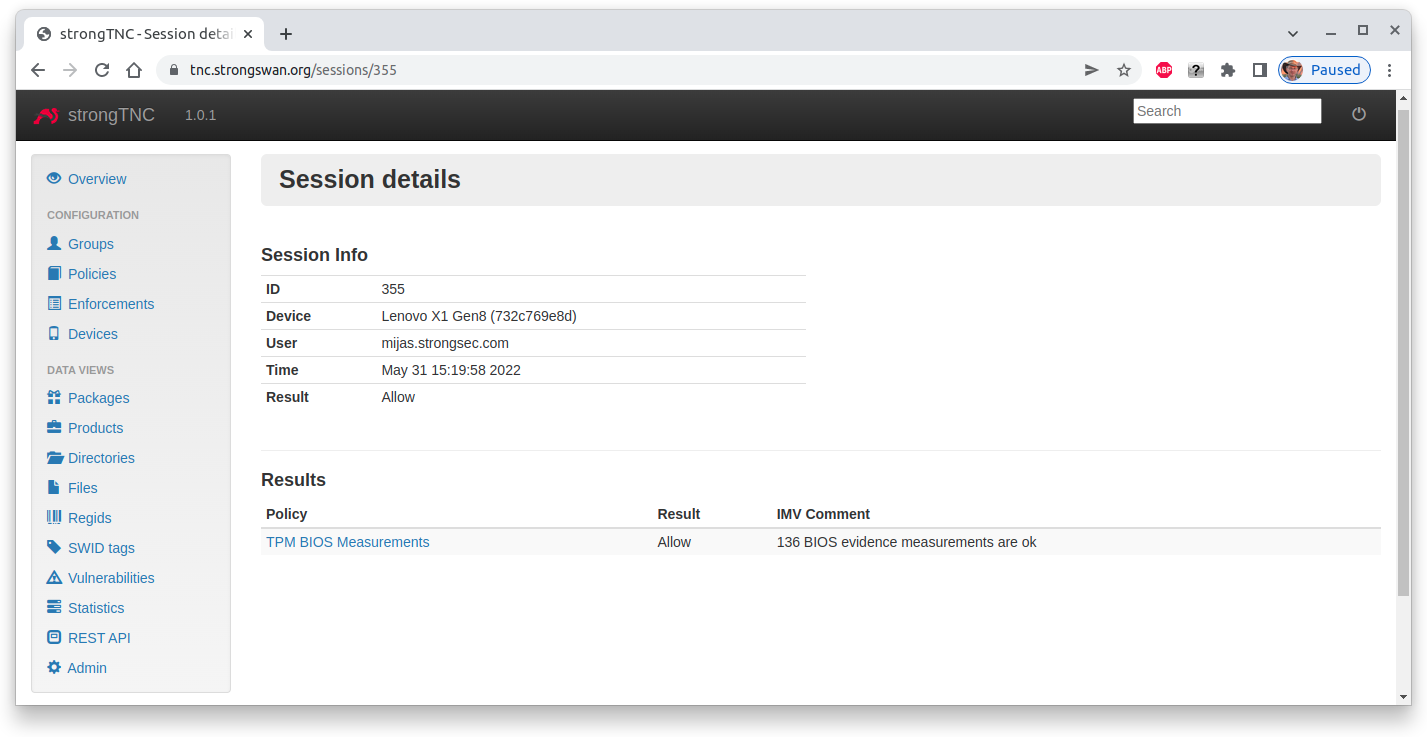
During the second and each subsequent run the received BIOS measurements are compared with the 136 reference values stored in the TPM Evidence table.
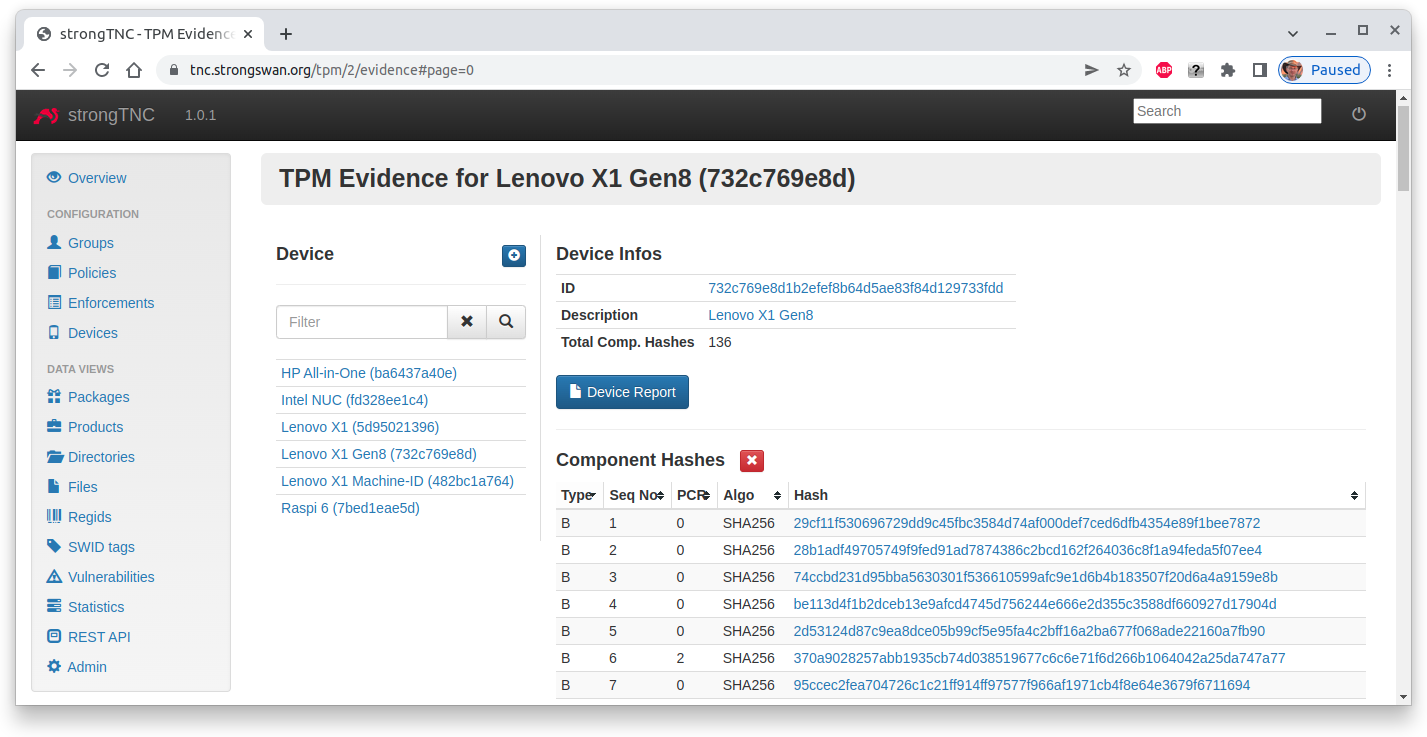
TPM Evidence
The registered BIOS measurements are stored in the TPM Evidence table and correspond
to the PCR Boot Event Log. Only
the SHA256 hashes but not the log entries are transferred by the
Attestation IMC to the
Attestation IMV.
The PCR Boot Event Log shows that
several bootload events (104, 105, 131..136) depend on the Linux kernel
version. Thus after a kernel update and a subsequent reboot on the endpoint, these
SHA256 hashes change, so that currently all Component Hashes have to be cleared
using the red Delete button.
Attestation Client
The Attestation Client is the TNC component located on the client side, retrieving and transmitting the TPM BIOS evidence.
Attestation Server
The Attestation Server is the TNC component running on the server side, receiving the TPM BIOS evidence and storing or verifying it in the strongTNC database.