Integrity Measurement Architecture
The Linux Integrity Measurement Architecture (IMA) maintains a runtime measurement list and, if anchored in a hardware Trusted Platform Module (TPM), an aggregate integrity value over this list. The benefit of anchoring the aggregate integrity value in the TPM is that the measurement list cannot be compromised by any software attack without being detectable. Hence on a trusted boot system, IMA can be used to attest the system’s runtime integrity.
strongTNC IMA Database
TPM BIOS/IMA Measurements and SW ID Subscription Policy
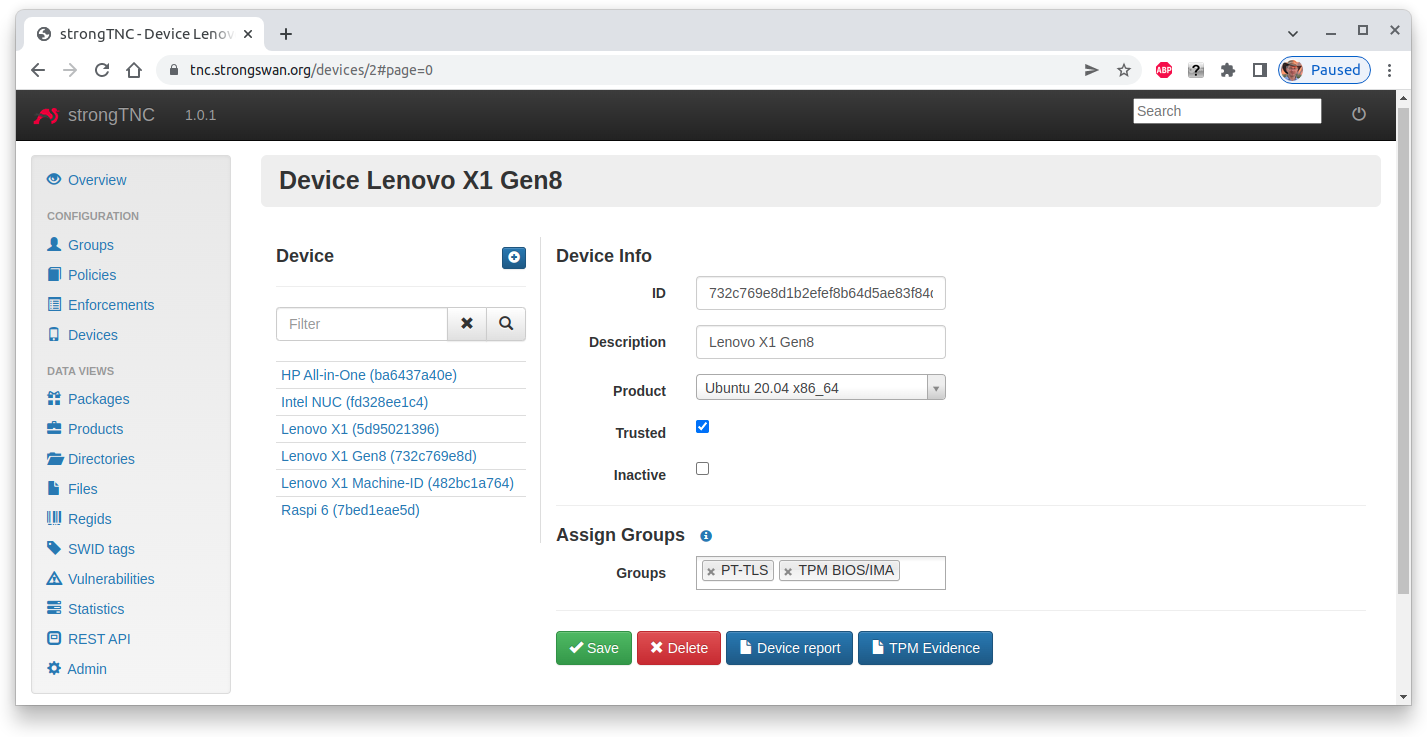
In order to enable BIOS and IMA measurements, add the TPM BIOS/IMA group
in the Device Info menu for a given device.
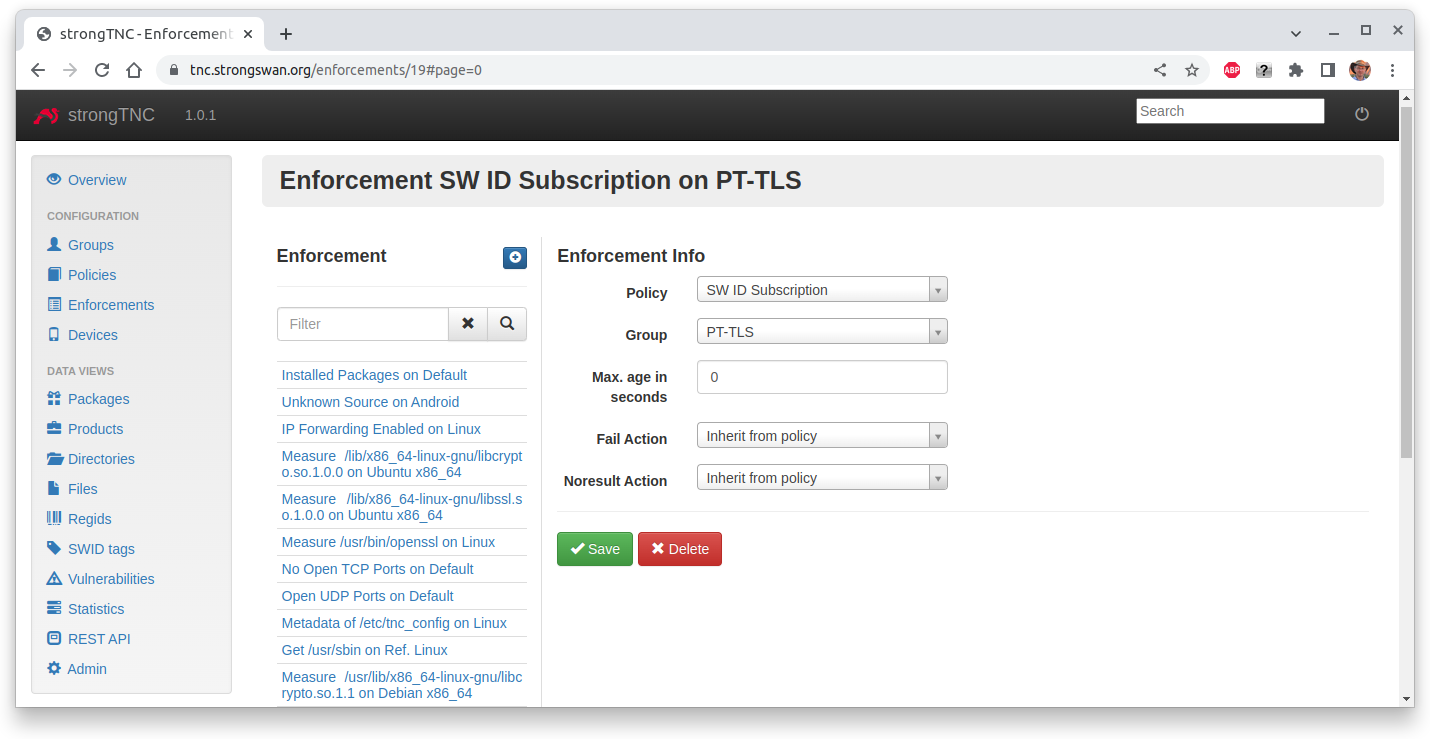
Since IMA measurements needs current file reference hashes, the
SW ID Subscription Policy is added via a special PT-TLS group.
Additionally set the Trusted flag in order to put trust into the Attestation Key
sent by the endpoint via the PA-TNC protocol. The Device ID is the keyid of
the AK, so that the correctness of the public key can be verified.
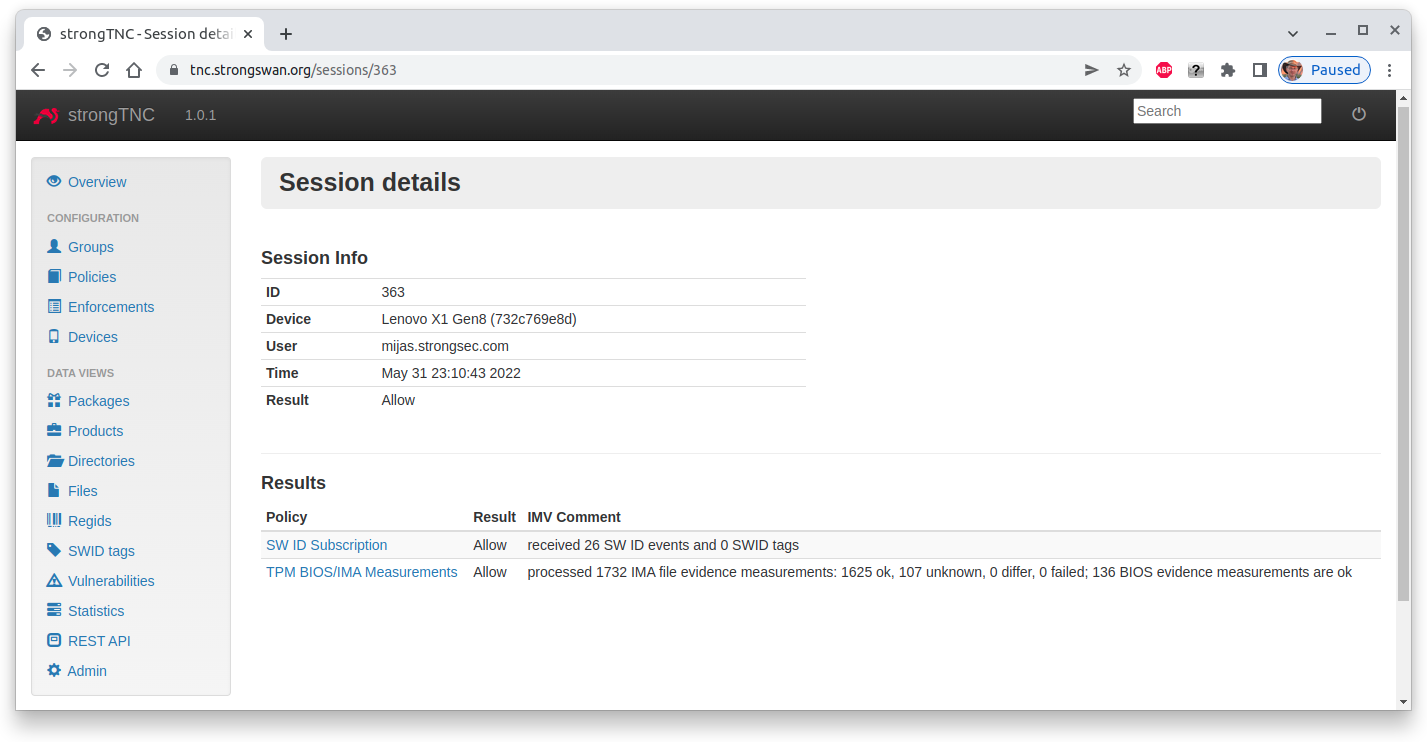
Device Report
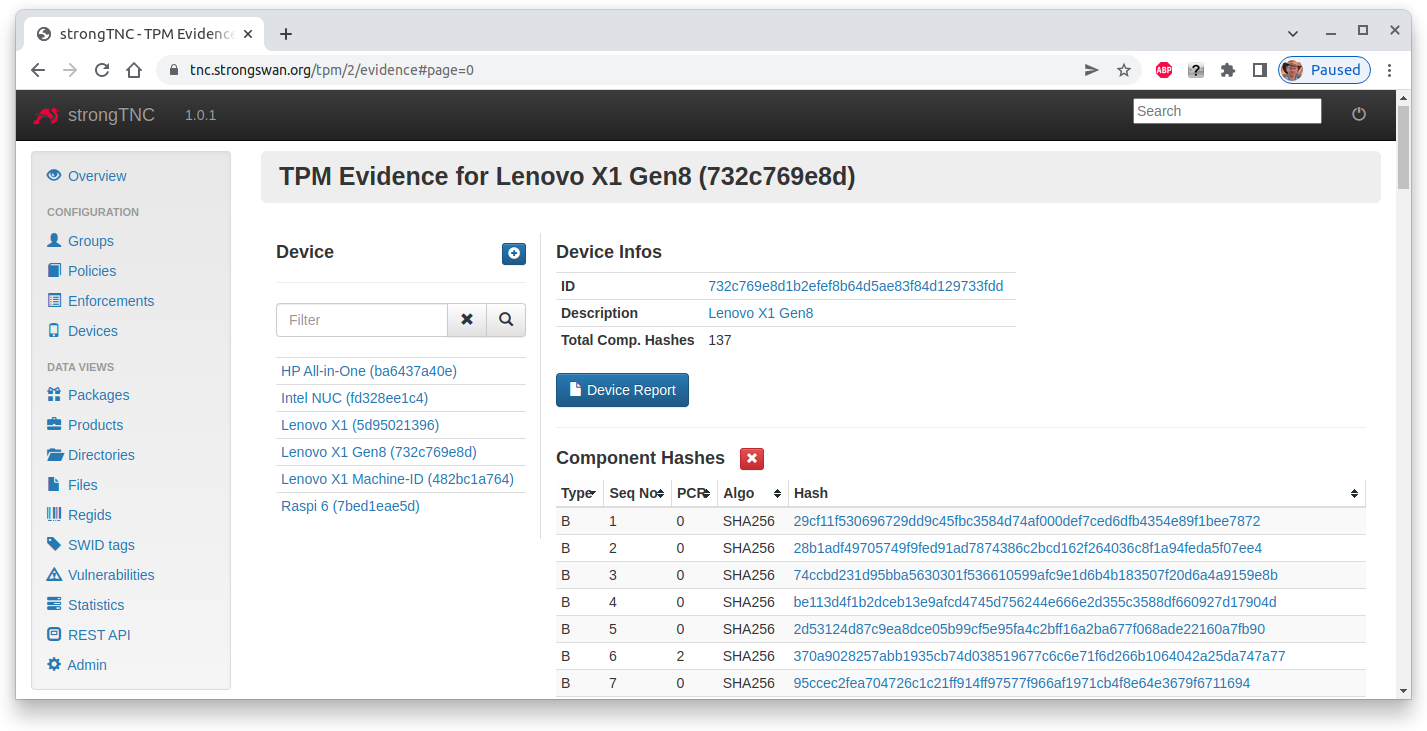
The session details of the device report show that 26 SW ID events, 1732 IMA measurements and 136 BIOS measurements were received and successfully verified.
IMA Client
The IMA Client is the TNC component located on the client
side, retrieving and transmitting the TPM BIOS and IMA evidence measurements and
updating the file hashes via the collector.db database.
IMA Server
The IMA Server is the TNC component running on the server side, receiving the TPM BIOS evidence measurements and storing or verifying them in the strongTNC database. The received IMA evidence measurements are compared with the reference file hashes stored in the strongTNC database that are periodically updated.